Troubleshooting ADFS authentication errors
This page describes the most frequent problems when implementing ADFS in your Octopus environment.
This information does not replace the expertise needed in your organization to implement single sign-on via ADFS.
Verification of the certificate held by your Octopus environment
For performance reasons, the Octopus server caches the thumbprint of your identity federation server's certificate. This certificate will necessarily expire eventually. Normally, you must replace this certificate before it expires to avoid service interruption. When the Octopus server realizes that the certificate has expired, it will contact your identity federation server again to obtain the new version of the certificate.
How to test ?
- Access the identity federation configuration page
- Start Octopus
-
Tools > Identity Federation Configuration
-
Download the certificate by pressing the View Certificate button on the identity federation server
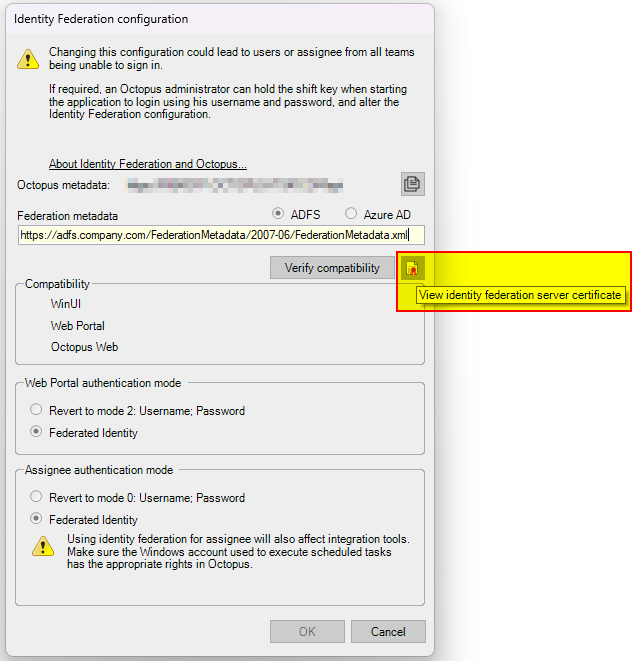
- Specify a location to save the file
-
The certificate will then be automatically displayed
* Only administrators with permissions to change authentication settings will be able to log in.
The following permissions are required:* Administer Octopus
* Modify data common to all teams
To access the application, they will need to hold down the Shift key to be prompted for username/password. They can then temporarily disable federation to return to the previous mode.
In case of emergency, we can assign a new password to your administrator to allow access.
Result
For this test to be successful, you must validate that
- the certificate information matches the certificate on your ADFS server
- This certificate is not expired or invalid
Verify the Service Federation Server Configuration (FederationMetadata.xml)
This file is essential for the proper communication between your Octopus hosted environment and your service federation server. In order for the Octopus server to be able to communicate with your service federation server, you must ensure that you have publicly exposed this configuration file.
How to test ?
- Get the configuration URL you injected into Octopus
- Start Octopus
- Tools > Identity Federation Configuration
- Copy URL under Federation Metadata
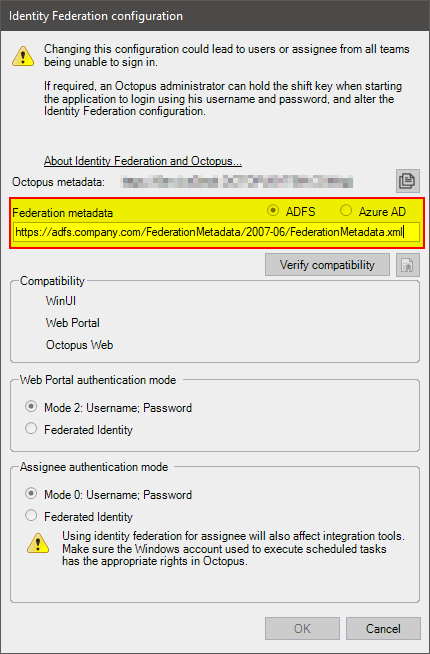
- Open an Internet browser in private mode (or Incognito)
- Access the URL copied in step 3
- This test is to be done with a browser
- connected to your corporate networke
- not connected to your corporate network
- This test is to be done with a browser
Result
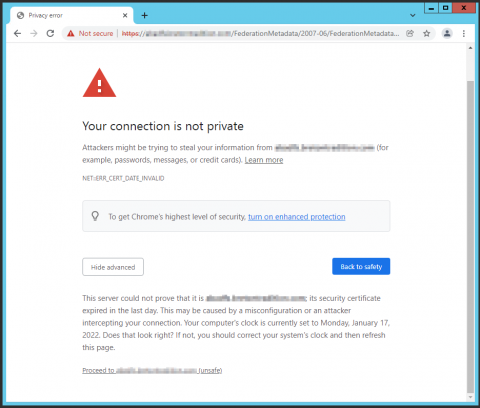
For this test to be successful, you must have been able to download this file (FederationMetadata.xml) without certificate errors or authentication requests.
This file contains non-sensitive information related to the configuration of your service federation server.
For example, you should NOT have a page that looks like this:
Thank you, your message has been sent.
